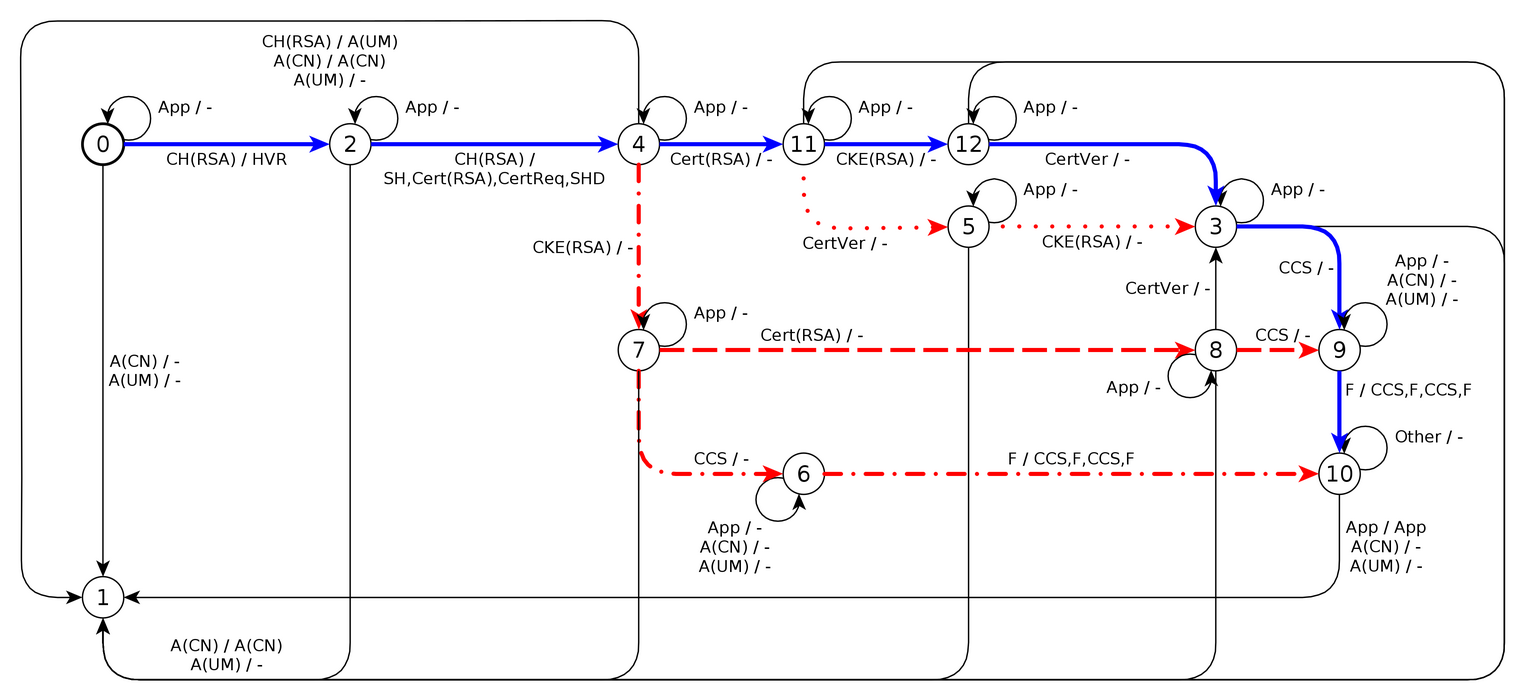
In our work, we analyze DTLS implementations using state learning methods and uncover several nice bugs in widely used libraries. For example, we found a client-authentication bypass in JSSE (CVE-2020-2655), the default (D)TLS stack used in Java.
You can read the preliminary paper version here:
https://www.usenix.org/conference/usenixsecurity20/presentation/fiterau-brostean
Or, you can already watch a talk presented by Robert Merget at RuhrSec 2020:
https://www.youtube.com/watch?v=alev9G2wNFk
This was a joint work with Uppsala University, Ruhr University Bochum, and SIDN Labs.