Paarungsbasierte Kryptographie
Paarungen sind bilineare Abbildungen, die sich zur Realisierung verschiedener kryptographischer Primitiven eignen. Damit bietet die paarungsbasierte Kryptographie Lösungsansätze für eine Vielzahl interessanter Probleme wie zum Beispiel
- Attributbasierte Kryptographie
- Anonyme Gruppensignaturen und Reputationssysteme
- Feingranuläre Zugangsberechtigungssysteme (Anonymous Credential Systems)
Bekannt wurde die paarungsbasierte Kryptographie besonders im Zusammenhang der identitätsbasierten Kryptographie. Hier handelt es sich um spezielle asymmetrische Verschlüsselungs- und Signaturverfahren. Die Besonderheit liegt in der Beschaffenheit des öffentlichen Schlüssels, der sich direkt aus der Identität des Besitzers ableiten lässt. So könnte beispielsweise eine Email mit einem, aus der Empfängeradresse abgeleiteten Schlüssel verschlüsselt werden. So entfällt die Kontaktierung eines zentralen Schlüsselcenters auf Seiten des Absenders. Das Schlüsselcenter wird stattdessen für die Generierung der privaten Schlüssel benötigt, muss also für jeden Teilnehmer nur einmal kontaktiert werden. Da das Schlüsselcenter alle privaten Schlüssel des Systems generiert, stellt es einen besonders empfindlichen Angriffspunkt dar.
Wir beschäftigen uns hier mit der Entwicklung weiterer Verfahren im Bereich der paarungsbasierten Kryptographie. Weiterhin untersuchen wir die Implementierungen dieser Verfahren hinsichtlich Effizienz und Sicherheit.
Attributbasierte Kryptographie
Eine der größten Visionen moderner Kryptographie ist die Entwicklung der sogenannten Funktionalen Verschlüsselungsverfahren. Anders als bei herkömmlichen Verschlüsselungsverfahren, bei denen man eine Nachricht bzw. Daten für einen gewissen Empfänger verschlüsselt, bekommt jeder Nutzer bei den Funktionalen Verschlüsselungen einen privaten Schlüssel zu einer bestimmten Funktion, die seine Berechtigungen bestimmt. Die Nachricht wird dann einmalig verschlüsselt und jeder Nutzer lernt nicht die verschlüsselte Nachricht, sondern nur die Auswertung seiner Funktion an dieser Nachricht. Während man für allgemeine Funktionen schon bei der Definition der Sicherheit auf Probleme stößt, existieren voll funktionale Verschlüsselungsverfahren für viele Spezialfälle wie identitätsbasierte, attributbasierte, prädikatbasierte Verschlüsselungsverfahren und viele andere.
Bei den sogenannten Key-Policy Attributbasierten Verschlüsselungsverfahren (KP-ABE) werden die Daten unter einer Menge von Attributen, welche die Daten bzw. die erlaubten Zugriffe darauf im gewissen Sinne beschreiben, verschlüsselt. Die Nutzer des Systems erhalten von der zentralen Instanz wiederum die geheimen Schlüssel, die deren Berechtigungen entsprechen. Vereinfacht, kann man sich so eine Berechtigung (Policy) als eine boolesche Formel über den Attributen des Systems vorstellen. Nur wenn die Attribute des Chiphertextes zu den Berechtigungen des Nutzers passen (d.h. die boolesche Formel ist durch die Attribute erfüllt), kann der Nutzer die verschlüsselte Nachricht mit Hilfe des geheimen Schlüssels komplett entschlüsseln. Bei den sogenannten Ciphertext-Policy Attributbasierten Verschlüsselungsverfahren (CP-ABE) sind wiederum die geheimen Schlüssel mit den Attributen versehen, während unter einer Policy verschlüsselt wird.
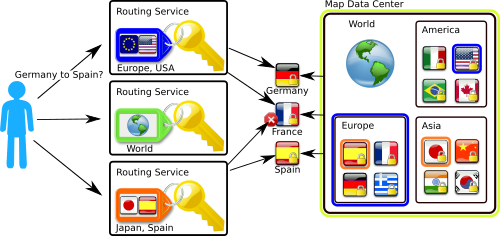
In dem folgenden Beispiel möchte ein Kartenanbieter feingranulare Zugriffe auf das Kartenmaterial realisieren. Dazu werden die einzelnen Karten unter den entsprechenden Policies (CP-ABE) verschlüsselt und auf einem öffentlich zugänglichen Datenserver zur Verfügung gestellt. Die Karte von Deutschland könnte man z.B. unter der Policy “World OR Europe OR Germany” verschlüsseln. Nun kann der Kartenanbieter seinen Kunden (z.B. Routing Anbietern) verschiedene Pakete anbieten. Je nach eingekauftem Produkt bekommt der Kunde einen passenden Schlüssel und somit den Zugang zum Kartenmaterial. Somit kann die Zugriffskontrolle durch die Verschlüsselung realisiert werden.
Anonyme Gruppensignaturen und Reputationssysteme
Bei klassischen digitalen Signaturverfahren berechnet ein Sender zu einer Nachricht eine Signatur, unter Verwendung eines geheimen Schlüssels. Mit Hilfe der Signatur und des öffentlichen Schlüssels des Senders kann ein Empfänger der Nachricht überprüfen, ob die Nachricht wirklich vom angegebenen Sender stammt oder ob sie verfälscht wurde. Um dies zu erreichen, muss der öffentliche Schlüssel zweifelsfrei dem Sender zugeordnet werden können. Diese Identifizierbarkeit ist allerdings in vielen Anwendungen nicht nötig oder gar unerwünscht. Sobald es für eine Anwendung ausreichend ist zu wissen, dass ein Sender einer gewissen Gruppe angehört, können anonyme Gruppensignaturen verwendet werden.
Anonyme Gruppensignaturen erlauben es Gruppenmitgliedern Nachrichten zu signieren, ohne dass sie ihre Identität offenbaren müssen. Hierzu erhält jedes Gruppenmitglied einen eigenen privaten Schlüssel, der zu einem öffentlichen Gruppenschlüssel passt. Im Gegensatz zu klassischen digitalen Signaturen kann von Nachrichtenempfängern nur noch überprüft werden, ob ein Gruppenmitglied eine Nachricht signiert hat, jedoch nicht bestimmen, welches Gruppenmitglied eine Nachricht signiert hat. Diese Möglichkeit hat nur ein ausgewiesener Gruppenmanager.
Neben der Anonymität spielen, je nach Anwendungsfall, auch andere Eigenschaften von Gruppensignaturen eine wichtige Rolle. Zum Beispiel kann es sinnvoll sein, Gruppenmitgliedern zu verbieten, mehr als eine bestimmte Anzahl an Nachrichten zu signieren. Ebenfalls wichtig sind Techniken zum Widerruf der Gruppenmitgliedschaft. Diese und andere Erweiterungen von Gruppensignaturen können unter anderen dazu genutzt werden, anonyme Reputationssysteme zu konstruieren.
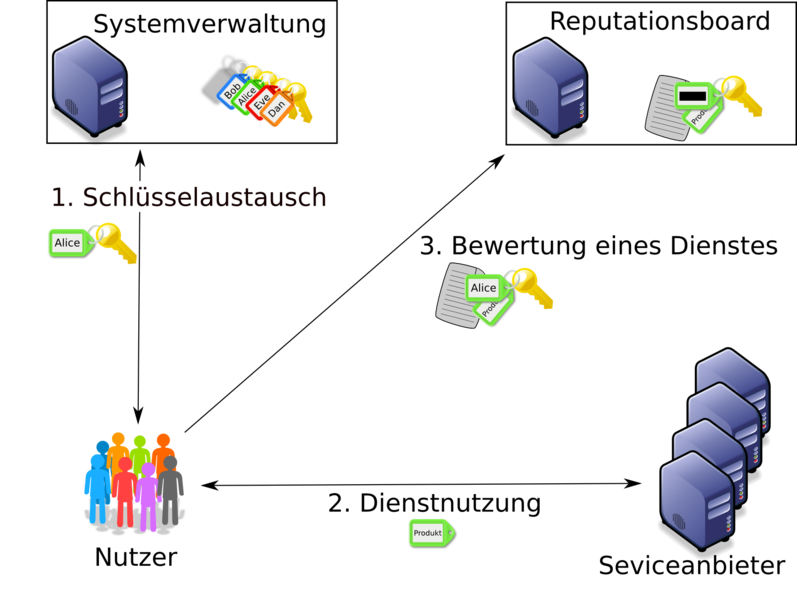
Reputationssysteme sind ein wichtiges Werkzeug, um Kunden und Anbietern von Waren oder Dienstleistungen wertvolle Informationen über frühere Transaktionen zu geben. Um vertrauenswürdige, zuverlässige und ehrliche Bewertungen zu erhalten, sollte ein Reputationssystem die Identität von Kunden schützen und gleichzeitig verhindern, dass Mehrfachbewertungen möglich sind. Selbstverständlich müssen die Bewertungen auch von Außenstehenden überprüft werden können.
Einige der geforderten Eigenschaften für Reputationssysteme sind von Gruppensignaturen bereits bekannt. Allerdings erfüllen sie nicht alle Anforderungen von Reputationssystemen. Diese bestehen nicht aus einer Gruppe - vielmehr gibt es für jedes zu bewertende Produkt (bzw. Dienstleistung) eine Gruppe. Bei der Betrachtung von Sicherheit solcher Systeme können also verschiedene Gruppensignaturen nicht in Isolation betrachtet werden.
Ziel dieses Forschungsbereiches ist die Erweiterung von Gruppensignaturverfahren und die Konstruktion von anonymen Reputationssystemen auf der Basis von Gruppensignaturen.
Feingranuläre Zugangsberechtigungssysteme (Anonymous Credential Systems)
Wie können wir einem Apotheker die Rezeptbesitzerlaubnis eines Patienten versichern ohne die Identität des Patienten zu nennen? Wie können wir als Autofahrer unsere Fahrlizens beweisen, ohne unseren Namen Preis zu geben? Für die Umsetzung dieser Szenarien benötigen wir anonyme Zugangsberechtigungssysteme. In Zugangsberechtigungssystemen erwerben Nutzer attribut-zertifizierte Zugangsberechtigungen. Diese Zugangsberechtigungen werden von Nutzern verwendet, um Zugriff auf bestimmte Ressourcen bzw. Services zu erhalten. Von besonderem Interesse sind Zugangsberechtigungssysteme, in denen Nutzern Attribute, und Ressourcen Policies über diesen Attributen zugewiesen werden. Der Nutzer kann auf eine Ressource zugreifen, wenn er nachweisen kann, dass seine Attribute die Policy der Ressource erfüllen. Wir interessieren uns für anonyme Zugangsberechtigungssysteme, deren Ressourcen-Policies besonders komplexe Strukturen besitzen, sogenannte feingranulare Zugangsberechtigungssysteme.
Damit ein Zugangsberechtigungssystem sicher ist, soll der Ressourcenzugriff eines Nutzers möglich sein, ohne die Identität dieses Nutzers zu erkennen. Neben der Anonymität der Nutzer soll auch garantiert werden, dass verschiedene Nutzer ihre Attribute nicht kombinieren können, um Zugriff auf eine Ressource zu bekommen. Für die Konstruktion sicherer Zugangsberechtigungssysteme, werden u.a. auf Paarungen basierte digitale Signaturverfahren verwendet.
Das Ziel dieses Forschungsbereichs ist die mathematisch-beweisbare Konstruktion sicherer feingranularer Zugangsberechtigungssysteme.
Sichere und effiziente Implementierung
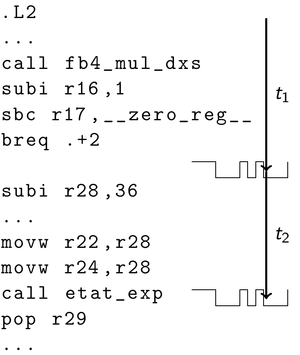
In den vergangenen Jahren wurden aufgrund der vielzähligen Anwendungsmöglichkeiten immer effizientere Algorithmen für die Berechnung von Paarungen entwickelt. Mittlerweile lassen sich Paarungen sogar in vertretbarer Zeit auf in ihren Ressourcen beschränkten Systemen, wie zum Beispiel Chipkarten berechnen. Dies ist besonders dann interessant, wenn die geheimen Schlüssel der Verfahren physikalisch gegen Angreifer geschütz werden müssen. Einem Angreifer mit physikalischem Zugriff auf die ausführende Hardware eines Verfahrens bieten sich zahlreiche Angriffspunkte, die in den Sicherheitsbeweisen der Verfahren normalerweise nicht berücksichtigt werden. Ein solcher, sogenannter Seitenkanalangreifer könnte zum Beispiel versuchen Informationen über den geheimen Schlüssel zu erlangen, indem er aktiv die Ausführung des Algorithmus manipuliert oder passiv Messgrößen wie Energieverbrauch und Ausführungszeit beobachtet.
Der Definitionsbereich einer Paarung sind Untergruppen einer elliptischen Kurve über einem endlichen Körper. Diese Strukturen bilden auch die Grundlagen für die Elliptische Kurven Kryptographie. Auf dem Gebiet der Seitenkanalresistenz Elliptischer Kurven Kryptographie gibt es bereits viele theoretische als auch praktische Ergebnisse. Teilweise lassen diese sich auch auf die paarungsbasierte Kryptographie übertragen. So können für aktive Angriffe die Fehlermechanismen, um die Ausführung eines Algorithmus zu manipulieren aus der Elliptischen Kurven Kryptographie auch hier angewandt werden. Für passive Angriffe lassen sich ebenfalls Analysemethoden übertragen, die aus Messwerten wie beispielsweise dem Energieverbrauch interessante Informationen extrahieren. Welche Manipulationen für einen Angreifer nützlich sind, und wie man aus den gewonnenen Informationen schließlich den geheimen Schlüssel eines Verfahrens extrahiert ist jedoch nicht einfach übertragbar. Dies liegt unter anderem an der komplizierteren Struktur der verwendeten Algorithmen und an der Rolle des geheimen Schlüssels für die Berechnung.
Ziel dieses Forschungsgebiets ist es die Sicherheit von paarungsbasierten Implementierungen zu verbessern und dazu relevante Seitenkanäle zu identifizieren und durch geeignete effiziente Gegenmaßnahmen zu schließen.
Publikationen
2023
A Formal Comparison of Advanced Digital Signature Primitives
P. Schürmann, A Formal Comparison of Advanced Digital Signature Primitives, 2023.
A Generic Construction of an Anonymous Reputation System and Instantiations from Lattices
J. Blömer, J. Bobolz, L.A. Porzenheim, in: 2023.
Designing Business Reputation Ecosystems — A Method for Issuing and Trading Monetary Ratings on a Blockchain
S. Hemmrich, J. Bobolz, D. Beverungen, J. Blömer, in: ECIS 2023 Research Papers, 2023.
On the impossibility of surviving (iterated) deletion of weakly dominated strategies in rational MPC
J. Blömer, J. Bobolz, H. Bröcher, in: 2023.
Privacy-Preserving Collection and Evaluation of Log Files
A. Koch, Privacy-Preserving Collection and Evaluation of Log Files, 2023.
Updatable Privacy-Preserving Reputation System based on Blockchain
M. Pilot, Updatable Privacy-Preserving Reputation System Based on Blockchain, 2023.
2022
Bringing Structure to Structure-Preserving Signatures: Overview, Implementation and Comparison of Selected SPS Schemes
H. Siek, Bringing Structure to Structure-Preserving Signatures: Overview, Implementation and Comparison of Selected SPS Schemes, 2022.
Cost of Privacy-preserving SMPC Protocols for NN-Based Inference
A. Anonymous, Cost of Privacy-Preserving SMPC Protocols for NN-Based Inference, 2022.
Evaluating database systems relying on secure multiparty computation
A. Anonymous, Evaluating Database Systems Relying on Secure Multiparty Computation, 2022.
Modelling and Proving Security for a Secure MPC Protocol for Stable Matching
E. Vahle, Modelling and Proving Security for a Secure MPC Protocol for Stable Matching, 2022.
On Transforming Lattice-Based Cryptography to the Ring Setting
P. Kramer, On Transforming Lattice-Based Cryptography to the Ring Setting, 2022.
Privacy-Preserving Cryptography: Attribute-Based Signatures and Updatable Credentials
F. Eidens, Privacy-Preserving Cryptography: Attribute-Based Signatures and Updatable Credentials, 2022.
2021
Cryptimeleon: A Library for Fast Prototyping of Privacy-Preserving Cryptographic Schemes
J. Bobolz, F. Eidens, R. Heitjohann, J. Fell, (2021).
Issuer-Hiding Attribute-Based Credentials
J. Bobolz, F. Eidens, S. Krenn, S. Ramacher, K. Samelin, in: Cryptology and Network Security, Springer International Publishing, Cham, 2021.
2020
A Group Signature Scheme from Flexible Public Key Signatures and Structure-Preserving Signatures on Equivalence Classes
P. Schürmann, A Group Signature Scheme from Flexible Public Key Signatures and Structure-Preserving Signatures on Equivalence Classes, Universität Paderborn, 2020.
Comparison of Zero-Knowledge Range Proofs
P. Kramer, Comparison of Zero-Knowledge Range Proofs, Universität Paderborn, 2020.
Enhancing Security by Usage of Universal One-Way Hash Functions
T. Terfort, Enhancing Security by Usage of Universal One-Way Hash Functions, Universität Paderborn, 2020.
Privacy-Preserving Incentive Systems with Highly Efficient Point-Collection
J. Bobolz, F. Eidens, S. Krenn, D. Slamanig, C. Striecks, in: Proceedings of the 15th ACM Asia Conference on Computer and Communications Security (ASIA CCS ’20), ACM, New York, NY, USA, 2020.
2019
Efficient Finite-Field Arithmetic for Elliptic Curve Cryptography in Java
M. Pilot, Efficient Finite-Field Arithmetic for Elliptic Curve Cryptography in Java, Universität Paderborn, 2019.
Implementation and Comparison of Elliptic Curve Algorithms in Java
S. Scholz, Implementation and Comparison of Elliptic Curve Algorithms in Java, Universität Paderborn, 2019.
Rational Secure Multiparty Computation
H. Bröcher, Rational Secure Multiparty Computation, Universität Paderborn, 2019.
Updatable Anonymous Credentials and Applications to Incentive Systems
J. Blömer, J. Bobolz, D.P. Diemert, F. Eidens, in: Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security - CCS ’19, 2019.
2018
Cloud Architectures for Searchable Encryption
J. Blömer, N. Löken, in: Proceedings of the 13th International Conference on Availability, Reliability and Security, ARES 2018, ACM, New York, NY, USA, n.d., pp. 25:1--25:10.
Delegatable Attribute-based Anonymous Credentials from Dynamically Malleable Signatures
J. Blömer, J. Bobolz, in: ACNS 2018 Applied Cryptography & Network Security, n.d.
Enhanced Security of Attribute-Based Signatures
J. Blömer, F. Eidens, J. Juhnke, in: The International Conference on Cryptology And Network Security (CANS), Springer, 2018, pp. 235–255.
Fully-Featured Anonymous Credentials with Reputation System
K. Bemmann, J. Blömer, J. Bobolz, H. Bröcher, D.P. Diemert, F. Eidens, L. Eilers, J.F. Haltermann, J. Juhnke, B. Otour, L.A. Porzenheim, S. Pukrop, E. Schilling, M. Schlichtig, M. Stienemeier, in: Proceedings of the 13th International Conference on Availability, Reliability and Security - ARES ’18, ACM, New York, NY, USA, n.d.
Models and Constructions for Secure Reputation Systems
J. Juhnke, Models and Constructions for Secure Reputation Systems, Universität Paderborn, 2018.
Practical, Anonymous, and Publicly Linkable Universally-Composable Reputation Systems
J. Blömer, F. Eidens, J. Juhnke, in: Topics in Cryptology - {CT-RSA} 2018 - The Cryptographers’ Track at the {RSA} Conference 2018, Proceedings, Springer International Publishing, Cham, 2018, pp. 470–490.
Provably Anonymous Communication Based on Trusted Execution Environments
J. Blömer, J. Bobolz, C. Scheideler, A. Setzer, Provably Anonymous Communication Based on Trusted Execution Environments, n.d.
Voronoi Cells of Lattices with Respect to Arbitrary Norms
J. Blömer, K. Kohn, SIAM Journal on Applied Algebra and Geometry. 2 (2018) 314–338.
2017
Attribute-Based Encryption as a Service for Access Control in Large-Scale Organizations
J. Blömer, P. Günther, V. Krummel, N. Löken, in: Foundations and Practice of Security, Springer International Publishing, Cham, 2017, pp. 3–17.
Attribute-based Signatures using Structure Preserving Signatures
P. Bemmann, Attribute-Based Signatures Using Structure Preserving Signatures, Universität Paderborn, 2017.
CCA-Security for Predicate Encryption Schemes
G. Liske, CCA-Security for Predicate Encryption Schemes, Universität Paderborn, 2017.
EAX - An Authenticated Encryption Mode for Block Ciphers
D. Diemert, EAX - An Authenticated Encryption Mode for Block Ciphers, Universität Paderborn, 2017.
Instantiating a Predicate Encryption Scheme via Pair Encodings
A. Ganesh Athreya, Instantiating a Predicate Encryption Scheme via Pair Encodings, Universität Paderborn, 2017.
Provably Secure Key-Derivation-Functions for Certain Types of Applications
M. Jürgens, Provably Secure Key-Derivation-Functions for Certain Types of Applications, Universität Paderborn, 2017.
Semantically Secure Attribute-based Searchable Encryption
D. Niehus, Semantically Secure Attribute-Based Searchable Encryption, Universität Paderborn, 2017.
Subtleties in Security Definitions for Predicate Encryption with Public Index
J. Blömer, G. Liske, in: Proceedings of the International Conference of Mathematical Aspects of Computer and Information Sciences (MACIS), Springer International Publishing, Cham, 2017, pp. 438–453.
2016
Commitment Schemes - Definitions, Variants, and Security
K.S. Bemmann, Commitment Schemes - Definitions, Variants, and Security, Universität Paderborn, 2016.
Comparison of different Definitions of Chosen-Ciphertext Security in Encryption schemes
L. Porzenheim, Comparison of Different Definitions of Chosen-Ciphertext Security in Encryption Schemes, Universität Paderborn, 2016.
Construction of Fully CCA-Secure Predicate Encryptions from Pair Encoding Schemes
J. Blömer, G. Liske, in: Proceedings of the CT-RSA 2016, 2016, pp. 431–447.
Physical attacks on pairing-based cryptography
P. Günther, Physical Attacks on Pairing-Based Cryptography, Universität Paderborn, 2016.
Short Randomizable Aggregatable Signatures: Constructions and Security Analysis
F. Dallmeier, Short Randomizable Aggregatable Signatures: Constructions and Security Analysis, Universität Paderborn, 2016.
Symmetric Anonymous Credentials with Protocols for Relations on Attributes
J. Hamm, Symmetric Anonymous Credentials with Protocols for Relations on Attributes, Universität Paderborn, 2016.
2015
A group signature scheme based on the LSRW assumption
F. Heihoff, A Group Signature Scheme Based on the LSRW Assumption, Universität Paderborn, 2015.
A Group Signature Scheme with Distributed Group Management - An Application of Threshold Encryption
N. Löken, A Group Signature Scheme with Distributed Group Management - An Application of Threshold Encryption, Universität Paderborn, 2015.
Anonymous and Publicly Linkable Reputation Systems
J. Blömer, J. Juhnke, C. Kolb, in: Proceedings of the 18th International Conference on Financial Cryptography and Data Security (FC), 2015, pp. 478--488.
Anonymous credential system based on q-Strong Diffie-Hellman Assumption
F. Eidens, Anonymous Credential System Based on Q-Strong Diffie-Hellman Assumption, Universität Paderborn, 2015.
Constructions of Fully Secure Predicate Encryption Schemes
P. Schleiter, Constructions of Fully Secure Predicate Encryption Schemes, Universität Paderborn, 2015.
Efficient Attributes for Pairing-Based Anonymous Credentials
C. Stroh, Efficient Attributes for Pairing-Based Anonymous Credentials, Universität Paderborn, 2015.
Efficient Verifier-Local Revocation for Anonymous Credentials
J. Bobolz, Efficient Verifier-Local Revocation for Anonymous Credentials, Universität Paderborn, 2015.
Elektromagnetische Seitenkanalangriffe auf paarungsbasierte Kryptographie
B. Gerken, Elektromagnetische Seitenkanalangriffe auf paarungsbasierte Kryptographie, Universität Paderborn, 2015.
Evaluation of Pairing Optimization for Embedded Platforms
M. Sosniak, Evaluation of Pairing Optimization for Embedded Platforms, Universität Paderborn, 2015.
Implementierung eines hybriden Verschlüsselungsverfahrens nach Cramer und Shoup
B. Kalde, Implementierung eines hybriden Verschlüsselungsverfahrens nach Cramer und Shoup, Universität Paderborn, 2015.
Number of Voronoi-relevant vectors in lattices with respect to arbitrary norms
K. Kohn, Number of Voronoi-Relevant Vectors in Lattices with Respect to Arbitrary Norms, Universität Paderborn, 2015.
Protokolle zur authentifizierten Schüsselvereinbarung
T. Eisenhofer, Protokolle zur authentifizierten Schüsselvereinbarung, Universität Paderborn, 2015.
Short Group Signatures with Distributed Traceability
J. Blömer, J. Juhnke, N. Löken, in: Proceedings of the Sixth International Conference on Mathematical Aspects of Computer and Information Sciences (MACIS), 2015, pp. 166–180.
Voronoi Cells of Lattices with Respect to Arbitrary Norms
J. Blömer, K. Kohn, Voronoi Cells of Lattices with Respect to Arbitrary Norms, Universität Paderborn, 2015.
2014
A Practical Second-Order Fault Attack against a Real-World Pairing Implementation
J. Blömer, R. Gomes da Silva, P. Günther, J. Krämer, J.-P. Seifert, in: Proceedings of Fault Tolerance and Diagnosis in Cryptography(FDTC), 2014, pp. 123--136.
Constructing CCA-secure predicate encapsulation schemes from CPA-secure schemes and universal one-way hash functions
J. Blömer, G. Liske, (2014).
Fujisaki-Okamoto Transformation
J. Lippert, Fujisaki-Okamoto Transformation, Universität Paderborn, 2014.
Group Signature Schemes with Strong Exculpability
P. Bemmann, Group Signature Schemes with Strong Exculpability, Universität Paderborn, 2014.
Hiding software components using functional encryption
J. Jochheim, Hiding Software Components Using Functional Encryption, Universität Paderborn, 2014.
RSA-Full Domain Hash Revisited
T. Rath, RSA-Full Domain Hash Revisited, Universität Paderborn, 2014.
Tampering attacks in pairing-based cryptography
J. Blömer, P. Günther, G. Liske, in: Proceedings of Fault Tolerance and Diagnosis in Cryptography(FDTC), 2014, pp. 1--7.
2013
Attributbasierte Verschlüsselung mittels Gittermethoden - Mathematische Grundlagen, Verfahren und Sicherheitsbeweise
K. Kohn, Attributbasierte Verschlüsselung mittels Gittermethoden - Mathematische Grundlagen, Verfahren und Sicherheitsbeweise, Universität Paderborn, 2013.
Direct Chosen-Ciphertext Secure Attribute-Based Key Encapsulations without Random Oracles
J. Blömer, G. Liske, (2013).
Securing Critical Unattended Systems with Identity Based Cryptography - A Case Study
J. Blömer, P. Günther, V. Krummel, in: Proceedings of the 5th International Conference on Mathematical Aspects of Computer and Information Sciences (MACIS), 2013, pp. 98–105.
Security Proofs for Pairing-Based Cryptography in the Generic Group Model
J. Bobolz, Security Proofs for Pairing-Based Cryptography in the Generic Group Model, Universität Paderborn, 2013.
Seitenkanalresistenz paarungsbasierter Kryptographie
O. Otte, Seitenkanalresistenz paarungsbasierter Kryptographie, Universität Paderborn, 2013.
Verteilte Erstellung und Aktualisierung von Schlüsselservern in identitätsbasierten Verschlüsselungssystemen
A. Tezer, Verteilte Erstellung und Aktualisierung von Schlüsselservern in identitätsbasierten Verschlüsselungssystemen, Universität Paderborn, 2013.
2012
Attribute-basierte Verschlüsselung
P. Schleiter, Attribute-basierte Verschlüsselung, Universität Paderborn, 2012.
Identitätsbasierte Kryptographie - Implementierung von Paarungen für Körper der Charakteristik 2
T. Haarhoff, Identitätsbasierte Kryptographie - Implementierung von Paarungen für Körper der Charakteristik 2, Universität Paderborn, 2012.
Identitätsbasierte Signaturen - Ein Sicherheitsbeweis für Signaturen auf Grundlage von Gap-Diffie-Hellman-Gruppen mit Hilfe des Forking-Lemmas
N. Löken, Identitätsbasierte Signaturen - Ein Sicherheitsbeweis für Signaturen auf Grundlage von Gap-Diffie-Hellman-Gruppen mit Hilfe des Forking-Lemmas, Universität Paderborn, 2012.
2011
Fault attacks in pairing-based cryptography
G. Liske, Fault Attacks in Pairing-Based Cryptography, Universität Paderborn, 2011.
2009
Analyse und Evaluation eines identitätsbasierten Signcryption-Verfahrens
G. Liske, Analyse Und Evaluation Eines Identitätsbasierten Signcryption-Verfahrens, 2009.
Alle Publikationen anzeigen