Pairing-based Cryptography
Pairings are bilinear maps that enable the realization of several cryptographic primitives. Pairing-based cryptography offers approaches for numerous interesting problems, such as
- Attribute-based cryptography
- Anonymous group signatures and reputation systems
- Fine-granular access control systems (Anonymous Credential Systems)
Pairing-based cryptography was first known and utilized in the field of identity-based cryptography. Identity-based cryptography deals with special asymmetric encryption and signature schemes. In identity-based schemes, the public key can be directly derived from the owner's identity. For example, this would allow you to encrypt an email using a key locally derived from the recipient's email address. Hence there is no need for the usual process of contacting a central key authority to retrieve the recipient's public key. Instead, the key authority is used to generate the private keys, with the added benefit that it only has be contacted once by every user. Since the key authority generates all private keys in such a system, it represents an especially lucrative target for malicious attacks.
In our group, we develop new schemes in the field of pairing-based cryptography. Furthermore, we analyze implementations of such schemes with respect to efficiency and security.
Attribute-based Cryptography
Development of so-called functional encryption schemes is one of the main visions of modern cryptography. These encryption schemes should overcome the main disadvantages of conventional encryption schemes, namely that data is encrypted for a certain addressee and the access to the encrypted data is all or nothing. In the context of functional encryption schemes, every user receives a secret key which is parameterized with a certain function according to the access rights of the user. The data is encrypted only once and the user learn only the evaluation of their function on data and not necessarily the data themselves. While in general it is difficult to even just define the security requirements for this kind of encryption schemes, efficient encryption schemes for different restricted classes of functions are known. Attribute-based encryption (ABE) is a special case of functional encryption.
An attribute-based system requires a central authority which sets the system up and provides the user with their secret keys. In key-policy ABE (KP-ABE), the owner of data defines a subset of predefined attributes for data and encrypts it once using this set. In order to access the encrypted data, every user in the system receives a user secret key provided with an access policy according to the rights of the user. The key policies are Boolean formulas over predefined attributes. A user will be able to decrypt a ciphertext if and only if the attributes of the ciphertext satisfy the policy of his/her key. For ciphertext-policy ABE (CP-ABE) the roles of attributes and policies are reversed. That is, the data is encrypted under an access policy and the keys are provided for sets of attributes. Systems based on ABE have to model the access rights of the user in terms of attributes and access policies depending on concrete scenarios and concrete access pattern.
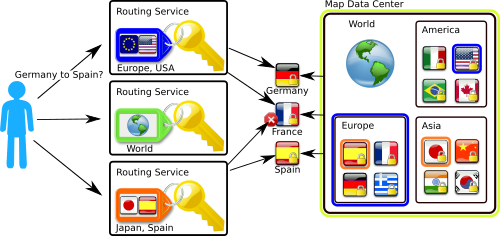
In our example, the manager of Map Data Center wants to ensure fine-grained access control to the road maps for its customers (routing services). Therefore, restricting access to the full data base, to the maps of continents, and to the maps of each single country will be realized. Each map is encrypted once with an appropriate policy. For example, the map of Germany's roads is encrypted with the policy "World OR Europe OR Germany". Every customer who gets a key with one of the attributes "World", "Europe", or "Germany", will be able to decrypt the appropriate ciphertext and obtain access to Germany's road maps. Thus, the access control is managed by the encryption itself.
Anonymous Group Signatures and Reputation Systems
In standard signature schemes, the sender computes a signature on his message using his secret key. The receiver can check, using the signature and the sender's public key, that the message was indeed composed by the sender and that it was not modified in transit. To achieve this, the public key must uniquely identify the sender. However, in many scenarios this strict identification is not necessary or even desirable. Whenever an application only needs assurance that the sender belongs to a certain group of possible senders, anonymous group signatures can be used.
Anonymous group signatures allow each member of a group to sign messages without disclosing their identity. For this, each group member gets their own private key that is associated to the group's public key. In contrast to standard digital signature schemes, the message receiver can only check whether some group member signed the message, but not which specific member did it. The actual signer can only be determined by a special entity in the system (the group manager).
Besides anonymity, other properties of group signatures play an important role in some applications. For example, it may be useful to restrict the number of messages that each group member can sign. Furthermore, techniques for revoking group membership are important. In particular, these and other extensions of group signatures can be used to construct anonymous reputation systems.
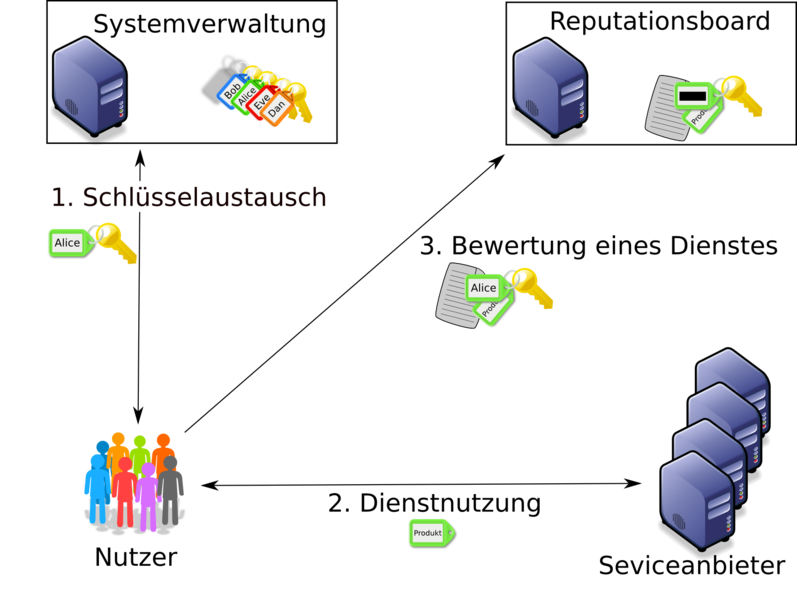
Reputation systems are an important tool to allow customers and providers of goods and services to gather useful information about past transactions. In order to receive trustworthy, reliable, and honest ratings, a reputation system should guarantee the customer anonymity and at the same ensure that no customer can submit more than one rating. Of course the ratings should be publicly verifiable by third parties.
Some of the required properties for reputation systems are already known for group signatures. Some, however, are not. For example, a reputation system does not consist of a single group, but rather there is a group for each rateable product (or service). For the security of reputation systems these different groups cannot be analyzed in isolation.
The goal of this research area is the extension of group signature schemes and the construction of anonymous reputation system on the basis of group signatures.
Anonymous Credential Systems
How can you assure a pharmacist that you have a prescription without revealing your identity? How can you show your driver's license without revealing your name? Such scenarios can be realized with anonymous credential systems. In such systems, users obtain credentials that certify attributes. With a credential, a user can access certain resources or services without revealing his identity. For this, he needs to prove that he is in possession of a credential with attributes that fulfill the resource's or service's access policy. We are interested in anonymous credential systems that support complex access policies.
In order for an anonymous credential system to be considered secure, the user must be able to access a resource without revealing his identity. Besides anonymity of users, credential systems must also make sure that users cannot collude and combine their attributes. A group of users must not be able to access to a resource for which none of the users (individually) have access to. Constructions of anonymous credentials usually rely on - among others - pairings and digital signatures.
The goal of this research area is to construct provably secure anonymous credential systems that support complex access policies.
Secure and Efficient Implementations
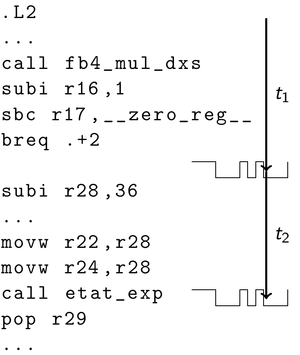
Because of the many applications of elliptic curves and pairings, increasingly more efficient algorithms to compute pairings have been developed in recent years. By now, pairings can even be computed in reasonably quickly on resource-restricted systems such as chip cards. This is particularly interesting if we want to defend against attackers with physical access to hardware executing computations that depend on a secret key. There are several ways to physically attack hardware which are usually not in the scope of formal security proofs. A physical attacker may try to gain information about the secret key by exploiting side channels. For example, the attacker may actively manipulate an algorithm's execution, or passively measure power consumption and running time.
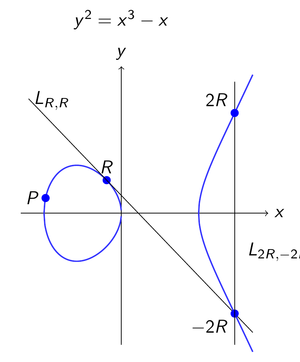
Pairings are defined on subgroups of elliptic curves over finite fields. These structures are also the basis for elliptic curve cryptography. There are already many theoretical and practical results on side-channel reistant elliptic curve cryptography. In part, these can be applied to pairing-based cryptography. For example, fault injection attacks on elliptic curve cryptography can be applied to pairing-based cryptography. For passive attacks, analysis methods for extracting information from power consumption can be applied as well. However, what cannot be easily applied to pairing-based cryptography are answers to the question "what manipulations are useful for an attacker?" and "how do I derive a secret key from data gathered through side channels?". This is because of the higher algorithm complexity and the role of the secret key for computations.
The goal of this research area is to improve security of pairing-based cryptography implemenations, to identify relevant side channels and to design efficient countermeasures against physical attackers.
Publications
2023
A Formal Comparison of Advanced Digital Signature Primitives
P. Schürmann, A Formal Comparison of Advanced Digital Signature Primitives, 2023.
A Generic Construction of an Anonymous Reputation System and Instantiations from Lattices
J. Blömer, J. Bobolz, L.A. Porzenheim, in: 2023.
Designing Business Reputation Ecosystems — A Method for Issuing and Trading Monetary Ratings on a Blockchain
S. Hemmrich, J. Bobolz, D. Beverungen, J. Blömer, in: ECIS 2023 Research Papers, 2023.
On the impossibility of surviving (iterated) deletion of weakly dominated strategies in rational MPC
J. Blömer, J. Bobolz, H. Bröcher, in: 2023.
Privacy-Preserving Collection and Evaluation of Log Files
A. Koch, Privacy-Preserving Collection and Evaluation of Log Files, 2023.
Updatable Privacy-Preserving Reputation System based on Blockchain
M. Pilot, Updatable Privacy-Preserving Reputation System Based on Blockchain, 2023.
2022
Bringing Structure to Structure-Preserving Signatures: Overview, Implementation and Comparison of Selected SPS Schemes
H. Siek, Bringing Structure to Structure-Preserving Signatures: Overview, Implementation and Comparison of Selected SPS Schemes, 2022.
Cost of Privacy-preserving SMPC Protocols for NN-Based Inference
A. Anonymous, Cost of Privacy-Preserving SMPC Protocols for NN-Based Inference, 2022.
Evaluating database systems relying on secure multiparty computation
A. Anonymous, Evaluating Database Systems Relying on Secure Multiparty Computation, 2022.
Modelling and Proving Security for a Secure MPC Protocol for Stable Matching
E. Vahle, Modelling and Proving Security for a Secure MPC Protocol for Stable Matching, 2022.
On Transforming Lattice-Based Cryptography to the Ring Setting
P. Kramer, On Transforming Lattice-Based Cryptography to the Ring Setting, 2022.
Privacy-Preserving Cryptography: Attribute-Based Signatures and Updatable Credentials
F. Eidens, Privacy-Preserving Cryptography: Attribute-Based Signatures and Updatable Credentials, 2022.
2021
Cryptimeleon: A Library for Fast Prototyping of Privacy-Preserving Cryptographic Schemes
J. Bobolz, F. Eidens, R. Heitjohann, J. Fell, (2021).
Issuer-Hiding Attribute-Based Credentials
J. Bobolz, F. Eidens, S. Krenn, S. Ramacher, K. Samelin, in: Cryptology and Network Security, Springer International Publishing, Cham, 2021.
2020
A Group Signature Scheme from Flexible Public Key Signatures and Structure-Preserving Signatures on Equivalence Classes
P. Schürmann, A Group Signature Scheme from Flexible Public Key Signatures and Structure-Preserving Signatures on Equivalence Classes, Universität Paderborn, 2020.
Comparison of Zero-Knowledge Range Proofs
P. Kramer, Comparison of Zero-Knowledge Range Proofs, Universität Paderborn, 2020.
Enhancing Security by Usage of Universal One-Way Hash Functions
T. Terfort, Enhancing Security by Usage of Universal One-Way Hash Functions, Universität Paderborn, 2020.
Privacy-Preserving Incentive Systems with Highly Efficient Point-Collection
J. Bobolz, F. Eidens, S. Krenn, D. Slamanig, C. Striecks, in: Proceedings of the 15th ACM Asia Conference on Computer and Communications Security (ASIA CCS ’20), ACM, New York, NY, USA, 2020.
2019
Efficient Finite-Field Arithmetic for Elliptic Curve Cryptography in Java
M. Pilot, Efficient Finite-Field Arithmetic for Elliptic Curve Cryptography in Java, Universität Paderborn, 2019.
Implementation and Comparison of Elliptic Curve Algorithms in Java
S. Scholz, Implementation and Comparison of Elliptic Curve Algorithms in Java, Universität Paderborn, 2019.
Rational Secure Multiparty Computation
H. Bröcher, Rational Secure Multiparty Computation, Universität Paderborn, 2019.
Updatable Anonymous Credentials and Applications to Incentive Systems
J. Blömer, J. Bobolz, D.P. Diemert, F. Eidens, in: Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security - CCS ’19, 2019.
2018
Cloud Architectures for Searchable Encryption
J. Blömer, N. Löken, in: Proceedings of the 13th International Conference on Availability, Reliability and Security, ARES 2018, ACM, New York, NY, USA, n.d., pp. 25:1--25:10.
Delegatable Attribute-based Anonymous Credentials from Dynamically Malleable Signatures
J. Blömer, J. Bobolz, in: ACNS 2018 Applied Cryptography & Network Security, n.d.
Enhanced Security of Attribute-Based Signatures
J. Blömer, F. Eidens, J. Juhnke, in: The International Conference on Cryptology And Network Security (CANS), Springer, 2018, pp. 235–255.
Fully-Featured Anonymous Credentials with Reputation System
K. Bemmann, J. Blömer, J. Bobolz, H. Bröcher, D.P. Diemert, F. Eidens, L. Eilers, J.F. Haltermann, J. Juhnke, B. Otour, L.A. Porzenheim, S. Pukrop, E. Schilling, M. Schlichtig, M. Stienemeier, in: Proceedings of the 13th International Conference on Availability, Reliability and Security - ARES ’18, ACM, New York, NY, USA, n.d.
Models and Constructions for Secure Reputation Systems
J. Juhnke, Models and Constructions for Secure Reputation Systems, Universität Paderborn, 2018.
Practical, Anonymous, and Publicly Linkable Universally-Composable Reputation Systems
J. Blömer, F. Eidens, J. Juhnke, in: Topics in Cryptology - {CT-RSA} 2018 - The Cryptographers’ Track at the {RSA} Conference 2018, Proceedings, Springer International Publishing, Cham, 2018, pp. 470–490.
Provably Anonymous Communication Based on Trusted Execution Environments
J. Blömer, J. Bobolz, C. Scheideler, A. Setzer, Provably Anonymous Communication Based on Trusted Execution Environments, n.d.
Voronoi Cells of Lattices with Respect to Arbitrary Norms
J. Blömer, K. Kohn, SIAM Journal on Applied Algebra and Geometry. 2 (2018) 314–338.
2017
Attribute-Based Encryption as a Service for Access Control in Large-Scale Organizations
J. Blömer, P. Günther, V. Krummel, N. Löken, in: Foundations and Practice of Security, Springer International Publishing, Cham, 2017, pp. 3–17.
Attribute-based Signatures using Structure Preserving Signatures
P. Bemmann, Attribute-Based Signatures Using Structure Preserving Signatures, Universität Paderborn, 2017.
CCA-Security for Predicate Encryption Schemes
G. Liske, CCA-Security for Predicate Encryption Schemes, Universität Paderborn, 2017.
EAX - An Authenticated Encryption Mode for Block Ciphers
D. Diemert, EAX - An Authenticated Encryption Mode for Block Ciphers, Universität Paderborn, 2017.
Instantiating a Predicate Encryption Scheme via Pair Encodings
A. Ganesh Athreya, Instantiating a Predicate Encryption Scheme via Pair Encodings, Universität Paderborn, 2017.
Provably Secure Key-Derivation-Functions for Certain Types of Applications
M. Jürgens, Provably Secure Key-Derivation-Functions for Certain Types of Applications, Universität Paderborn, 2017.
Semantically Secure Attribute-based Searchable Encryption
D. Niehus, Semantically Secure Attribute-Based Searchable Encryption, Universität Paderborn, 2017.
Subtleties in Security Definitions for Predicate Encryption with Public Index
J. Blömer, G. Liske, in: Proceedings of the International Conference of Mathematical Aspects of Computer and Information Sciences (MACIS), Springer International Publishing, Cham, 2017, pp. 438–453.
2016
Commitment Schemes - Definitions, Variants, and Security
K.S. Bemmann, Commitment Schemes - Definitions, Variants, and Security, Universität Paderborn, 2016.
Comparison of different Definitions of Chosen-Ciphertext Security in Encryption schemes
L. Porzenheim, Comparison of Different Definitions of Chosen-Ciphertext Security in Encryption Schemes, Universität Paderborn, 2016.
Construction of Fully CCA-Secure Predicate Encryptions from Pair Encoding Schemes
J. Blömer, G. Liske, in: Proceedings of the CT-RSA 2016, 2016, pp. 431–447.
Physical attacks on pairing-based cryptography
P. Günther, Physical Attacks on Pairing-Based Cryptography, Universität Paderborn, 2016.
Short Randomizable Aggregatable Signatures: Constructions and Security Analysis
F. Dallmeier, Short Randomizable Aggregatable Signatures: Constructions and Security Analysis, Universität Paderborn, 2016.
Symmetric Anonymous Credentials with Protocols for Relations on Attributes
J. Hamm, Symmetric Anonymous Credentials with Protocols for Relations on Attributes, Universität Paderborn, 2016.
2015
A group signature scheme based on the LSRW assumption
F. Heihoff, A Group Signature Scheme Based on the LSRW Assumption, Universität Paderborn, 2015.
A Group Signature Scheme with Distributed Group Management - An Application of Threshold Encryption
N. Löken, A Group Signature Scheme with Distributed Group Management - An Application of Threshold Encryption, Universität Paderborn, 2015.
Anonymous and Publicly Linkable Reputation Systems
J. Blömer, J. Juhnke, C. Kolb, in: Proceedings of the 18th International Conference on Financial Cryptography and Data Security (FC), 2015, pp. 478--488.
Anonymous credential system based on q-Strong Diffie-Hellman Assumption
F. Eidens, Anonymous Credential System Based on Q-Strong Diffie-Hellman Assumption, Universität Paderborn, 2015.
Constructions of Fully Secure Predicate Encryption Schemes
P. Schleiter, Constructions of Fully Secure Predicate Encryption Schemes, Universität Paderborn, 2015.
Efficient Attributes for Pairing-Based Anonymous Credentials
C. Stroh, Efficient Attributes for Pairing-Based Anonymous Credentials, Universität Paderborn, 2015.
Efficient Verifier-Local Revocation for Anonymous Credentials
J. Bobolz, Efficient Verifier-Local Revocation for Anonymous Credentials, Universität Paderborn, 2015.
Elektromagnetische Seitenkanalangriffe auf paarungsbasierte Kryptographie
B. Gerken, Elektromagnetische Seitenkanalangriffe auf paarungsbasierte Kryptographie, Universität Paderborn, 2015.
Evaluation of Pairing Optimization for Embedded Platforms
M. Sosniak, Evaluation of Pairing Optimization for Embedded Platforms, Universität Paderborn, 2015.
Implementierung eines hybriden Verschlüsselungsverfahrens nach Cramer und Shoup
B. Kalde, Implementierung eines hybriden Verschlüsselungsverfahrens nach Cramer und Shoup, Universität Paderborn, 2015.
Number of Voronoi-relevant vectors in lattices with respect to arbitrary norms
K. Kohn, Number of Voronoi-Relevant Vectors in Lattices with Respect to Arbitrary Norms, Universität Paderborn, 2015.
Protokolle zur authentifizierten Schüsselvereinbarung
T. Eisenhofer, Protokolle zur authentifizierten Schüsselvereinbarung, Universität Paderborn, 2015.
Short Group Signatures with Distributed Traceability
J. Blömer, J. Juhnke, N. Löken, in: Proceedings of the Sixth International Conference on Mathematical Aspects of Computer and Information Sciences (MACIS), 2015, pp. 166–180.
Voronoi Cells of Lattices with Respect to Arbitrary Norms
J. Blömer, K. Kohn, Voronoi Cells of Lattices with Respect to Arbitrary Norms, Universität Paderborn, 2015.
2014
A Practical Second-Order Fault Attack against a Real-World Pairing Implementation
J. Blömer, R. Gomes da Silva, P. Günther, J. Krämer, J.-P. Seifert, in: Proceedings of Fault Tolerance and Diagnosis in Cryptography(FDTC), 2014, pp. 123--136.
Constructing CCA-secure predicate encapsulation schemes from CPA-secure schemes and universal one-way hash functions
J. Blömer, G. Liske, (2014).
Fujisaki-Okamoto Transformation
J. Lippert, Fujisaki-Okamoto Transformation, Universität Paderborn, 2014.
Group Signature Schemes with Strong Exculpability
P. Bemmann, Group Signature Schemes with Strong Exculpability, Universität Paderborn, 2014.
Hiding software components using functional encryption
J. Jochheim, Hiding Software Components Using Functional Encryption, Universität Paderborn, 2014.
RSA-Full Domain Hash Revisited
T. Rath, RSA-Full Domain Hash Revisited, Universität Paderborn, 2014.
Tampering attacks in pairing-based cryptography
J. Blömer, P. Günther, G. Liske, in: Proceedings of Fault Tolerance and Diagnosis in Cryptography(FDTC), 2014, pp. 1--7.
2013
Attributbasierte Verschlüsselung mittels Gittermethoden - Mathematische Grundlagen, Verfahren und Sicherheitsbeweise
K. Kohn, Attributbasierte Verschlüsselung mittels Gittermethoden - Mathematische Grundlagen, Verfahren und Sicherheitsbeweise, Universität Paderborn, 2013.
Direct Chosen-Ciphertext Secure Attribute-Based Key Encapsulations without Random Oracles
J. Blömer, G. Liske, (2013).
Securing Critical Unattended Systems with Identity Based Cryptography - A Case Study
J. Blömer, P. Günther, V. Krummel, in: Proceedings of the 5th International Conference on Mathematical Aspects of Computer and Information Sciences (MACIS), 2013, pp. 98–105.
Security Proofs for Pairing-Based Cryptography in the Generic Group Model
J. Bobolz, Security Proofs for Pairing-Based Cryptography in the Generic Group Model, Universität Paderborn, 2013.
Seitenkanalresistenz paarungsbasierter Kryptographie
O. Otte, Seitenkanalresistenz paarungsbasierter Kryptographie, Universität Paderborn, 2013.
Verteilte Erstellung und Aktualisierung von Schlüsselservern in identitätsbasierten Verschlüsselungssystemen
A. Tezer, Verteilte Erstellung und Aktualisierung von Schlüsselservern in identitätsbasierten Verschlüsselungssystemen, Universität Paderborn, 2013.
2012
Attribute-basierte Verschlüsselung
P. Schleiter, Attribute-basierte Verschlüsselung, Universität Paderborn, 2012.
Identitätsbasierte Kryptographie - Implementierung von Paarungen für Körper der Charakteristik 2
T. Haarhoff, Identitätsbasierte Kryptographie - Implementierung von Paarungen für Körper der Charakteristik 2, Universität Paderborn, 2012.
Identitätsbasierte Signaturen - Ein Sicherheitsbeweis für Signaturen auf Grundlage von Gap-Diffie-Hellman-Gruppen mit Hilfe des Forking-Lemmas
N. Löken, Identitätsbasierte Signaturen - Ein Sicherheitsbeweis für Signaturen auf Grundlage von Gap-Diffie-Hellman-Gruppen mit Hilfe des Forking-Lemmas, Universität Paderborn, 2012.
2011
Fault attacks in pairing-based cryptography
G. Liske, Fault Attacks in Pairing-Based Cryptography, Universität Paderborn, 2011.
2009
Analyse und Evaluation eines identitätsbasierten Signcryption-Verfahrens
G. Liske, Analyse Und Evaluation Eines Identitätsbasierten Signcryption-Verfahrens, 2009.
Show all publications