Project group ReCoTroy
- Project group
- CS/CE Master's Program
- Lecture Number: L.079.07008
- Term: SS 2017 and WS 2017/2018
Goals
According to wikipedia, a computer trojan is a malicious piece of software, which is used to hack into a computer by misleading a user of its true intent. Hardware trojans are no different in this regard; they are malicious circuits instead of programs, capable of causing much damage or leaking lots of information, if they manage to avoid detection. In this project, we will focus on a new type of trojan: trojans in hardware modules (IP cores) of reconfigurable computers.
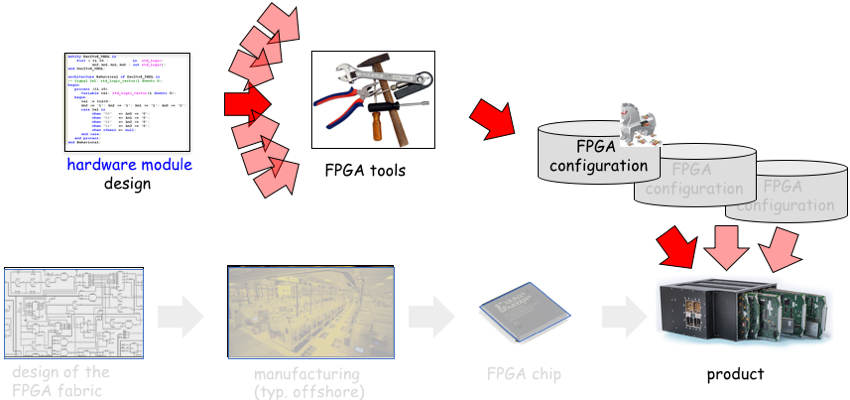
Reconfigurable computers are malleable hardware, whose function may be changed repeatedly at runtime, or put in another way, it is hardware that is reprogrammable like software. One example of such reconfigurable hardware devices are FPGAs (field programmable gate arrays). FPGAs can load configuration files to reconfigure their hardware functions, much like processors can load programs. With todays complex devices, creating a complete FPGA configuration from scratch is a daunting task, which is usually too costly to perform, so that nowadays FPGA designs usually are created using existing hardware modules as building blocks, so called IP cores (intellectual property cores), much like you would use libraries to reduce the effort of creating a new software program. And just as a trojan infected library could undermine a sofware program, an infected IP core is a large threat that could be lurking in FPGA configurations. Detecting such trojans before they are able to deliver their malicious payload, is a very hot research topic.
What you should bring with you
- Interest in embedded system design (hardware and/or software)
- Interest in security topics
- First experience with programming embedded processors (C/C++, compilers) and/or FPGAs (VHDL, design tools) is very helpful
What you will gain
- Knowledge about architectures and tools for embedded systems-on-chip
- Practical experience in embedded system design
- Expertise in the emerging field of hardware trojans
Optional: accompanying course in WS17/18 “Reconfigurable Computing”
Tasks
- Study and understand hardware trojans in reconfigurable modules
- Develop and demonstrate hardware trojan attacks
- Develop and demonstrate defenses against hardware trojans
Available for CS and CE students
This project group will be offered for both, computer science and computer engineering students. Because of the different regulations and ECTS credits of the CS and the CE program, the rules for participation also differ a bit.
- For computer science students the rules for participation are the same as for any other project group in the CS department (30 ECTS points for PG including a mandatory seminar part)
- For computer engineering the practical part of the project group is accounted like a regular CE project group (18 ECTS). The seminar is accounted as an additional elective course of the computer science specialization area (4 ECTS). To compensate the remaining difference in credits between the CS and CE program, the expected effort for the practical part will be adjusted accordingly.
Slides
You can download oour introduction slides from the project group presentation event here: Slides PG ReCoTroy.


